Labra for Co-sell AWS Resources
Information about AWS Resources used by Labra, their ownership and responsibilities
Labra enables the sync between ACE and your CRM, to make this possible, some setup with AWS Resources is required
AWS Resources
- S3 bucket
- KMS key
- IAM Role
Introducing some context:
- ACE AWS Account: account owned by ACE where Labra or Customer does not have access.
- Customer's AWS Account: any account that is owned by the customer.
- Labra's AWS Account: This is a production account where labra servers run.
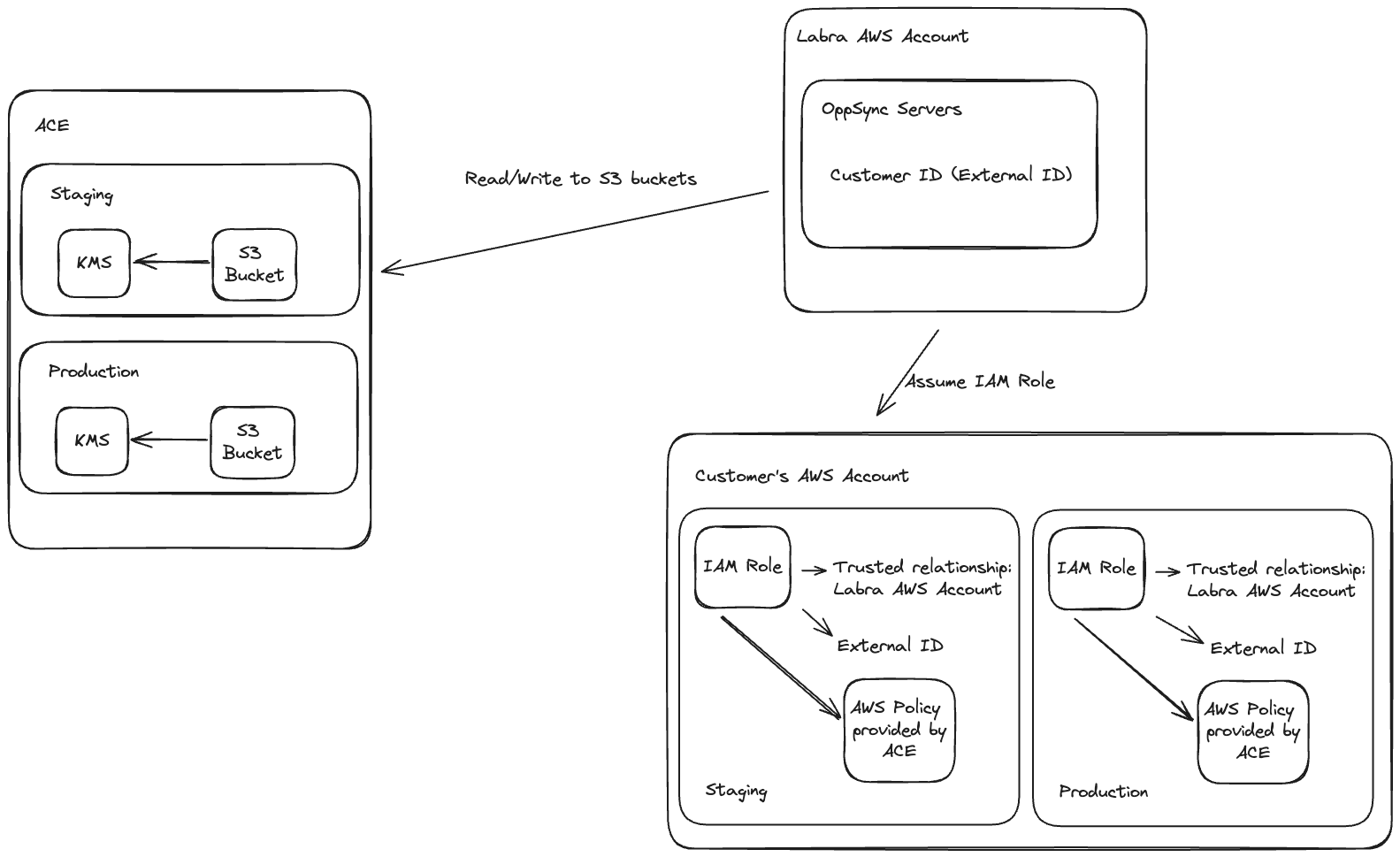
ACE Setup
S3 buckets
Once the 3rd party integration is enabled on ACE a 2 S3 buckets are created, these are owned and managed by ACE and live on ACE's AWS account. One bucket is for production and the other one is for staging (a.k.a beta)
The S3 bucket are used for the integration, because it has outbound and inbound folders where leads and opportunities flow through. Now to access folders we need to have special permissions.
IAM Roles
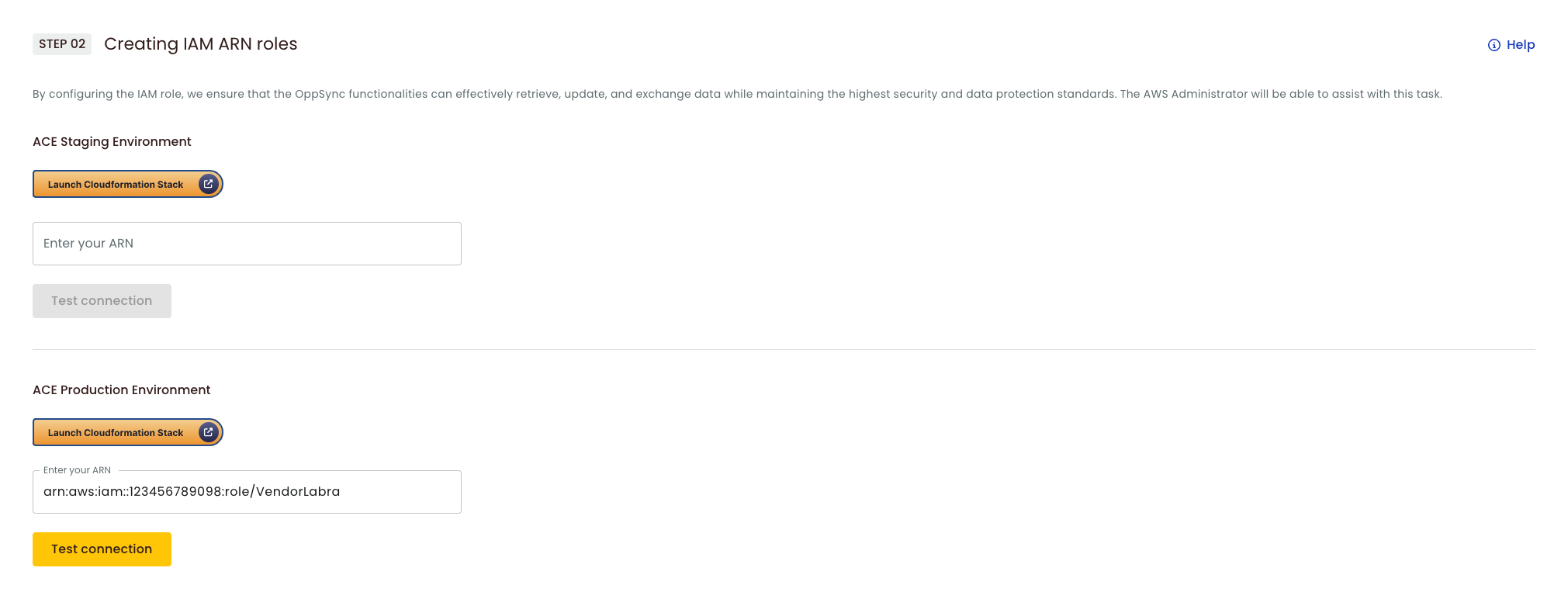
Labra interface to create an IAM Role with CloudFront template
An IAM Role will be required, one that will be live on Customer's AWS Account with a Trusted Relationship that includes the Account ID of Labra's AWS Account so Labra can assume the role and access the S3 bucket for the ACE integration in customer's behalf.
To create this IAM Role, the customer is asked to use this CloudFormation template which makes use of this template. The parameters will change based on the customer and if it is for staging or production. For extra security, the IAM Role can only be assumed with an External ID which is provided by Labra.
ACE AWS Policy
ACE will provide an AWS Policy that will need to be attached to the IAM Role mentioned before, notice only the customer can do this, since that account is owned by the customer.
An example of the AWS Policy is:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"kms:Encrypt",
"kms:DescribeKey",
"s3:ListBucket",
"kms:ReEncrypt*",
"kms:GenerateDataKey*"
],
"Resource": [
"arn:aws:s3:::ace-apn-33333-prod-us-west-2",
"arn:aws:kms:us-west-2:123456789012:key/df216356-609b-4c47-9af9-bd487ec63b0a"
]
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:DeleteObjectTagging",
"s3:PutObject",
"s3:GetObject",
"s3:GetObjectTagging",
"s3:PutObjectTagging",
"s3:DeleteObject",
"s3:PutObjectAcl"
],
"Resource": "arn:aws:s3:::ace-apn-33333-prod-us-west-2/*"
}
]
}
While the policy states that the actions PutObject, GetObject, DeleteObject, etc, can be executed, they can only be done in certain folders of that bucket, ACE has some restrictions, like for example only ACE can upload files into the outbound folder which means an opportunity or lead has been created/updated on ACE.
KMS
A KSM ARN is provided in the previous policy and it is used to encrypt and decrypt the contents of the S3 bucket, this is an standard practice by ACE.
Updated about 2 months ago
